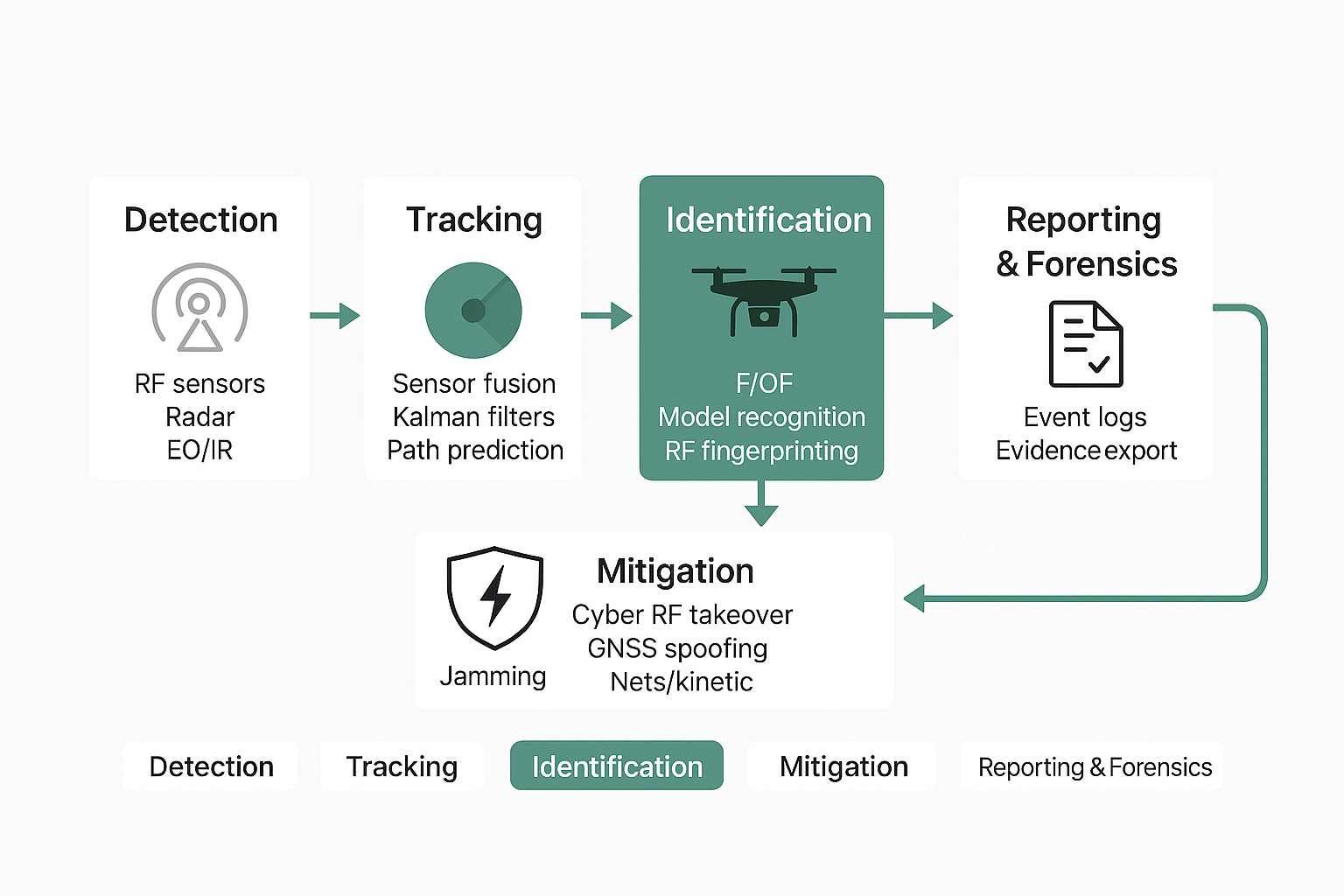
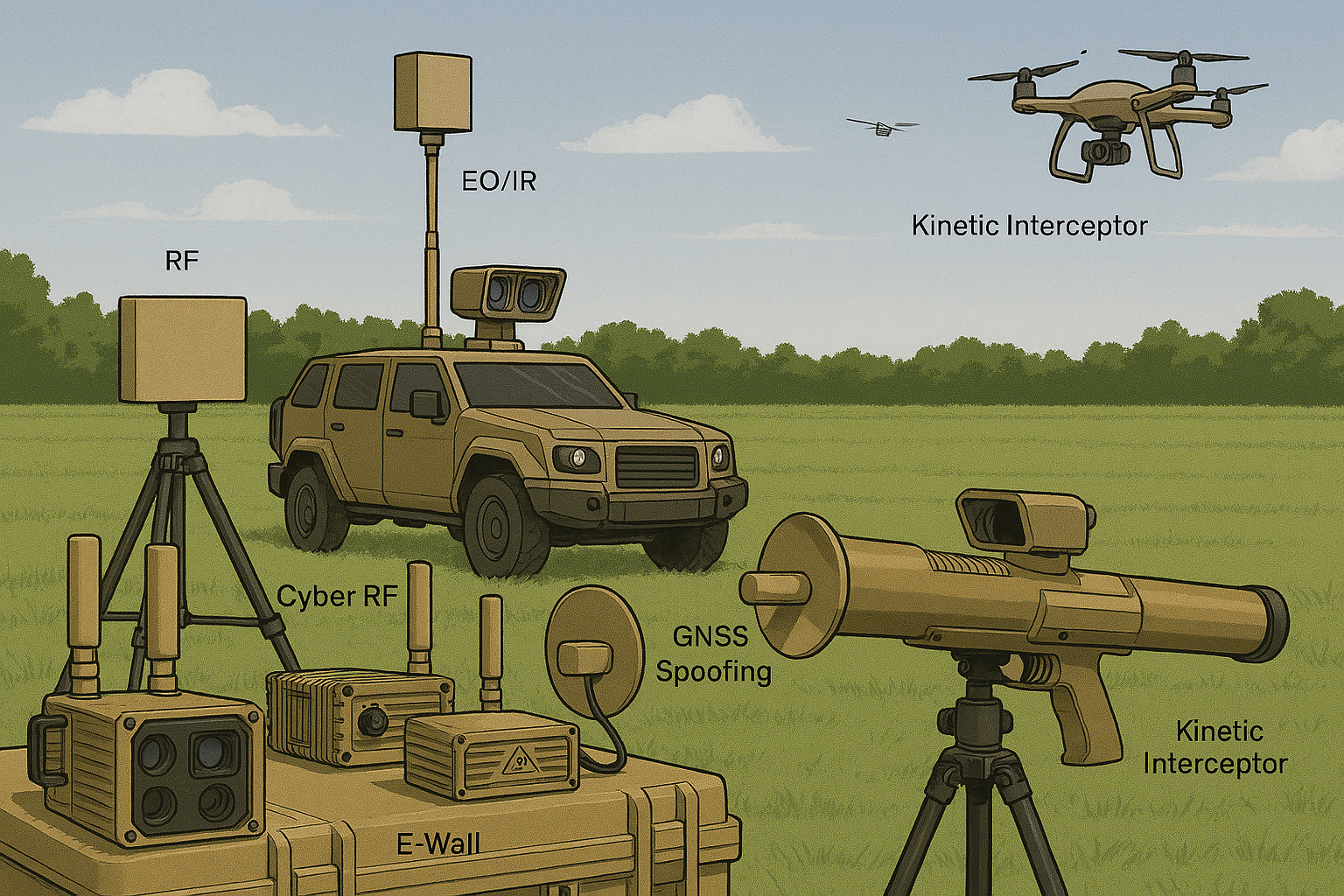
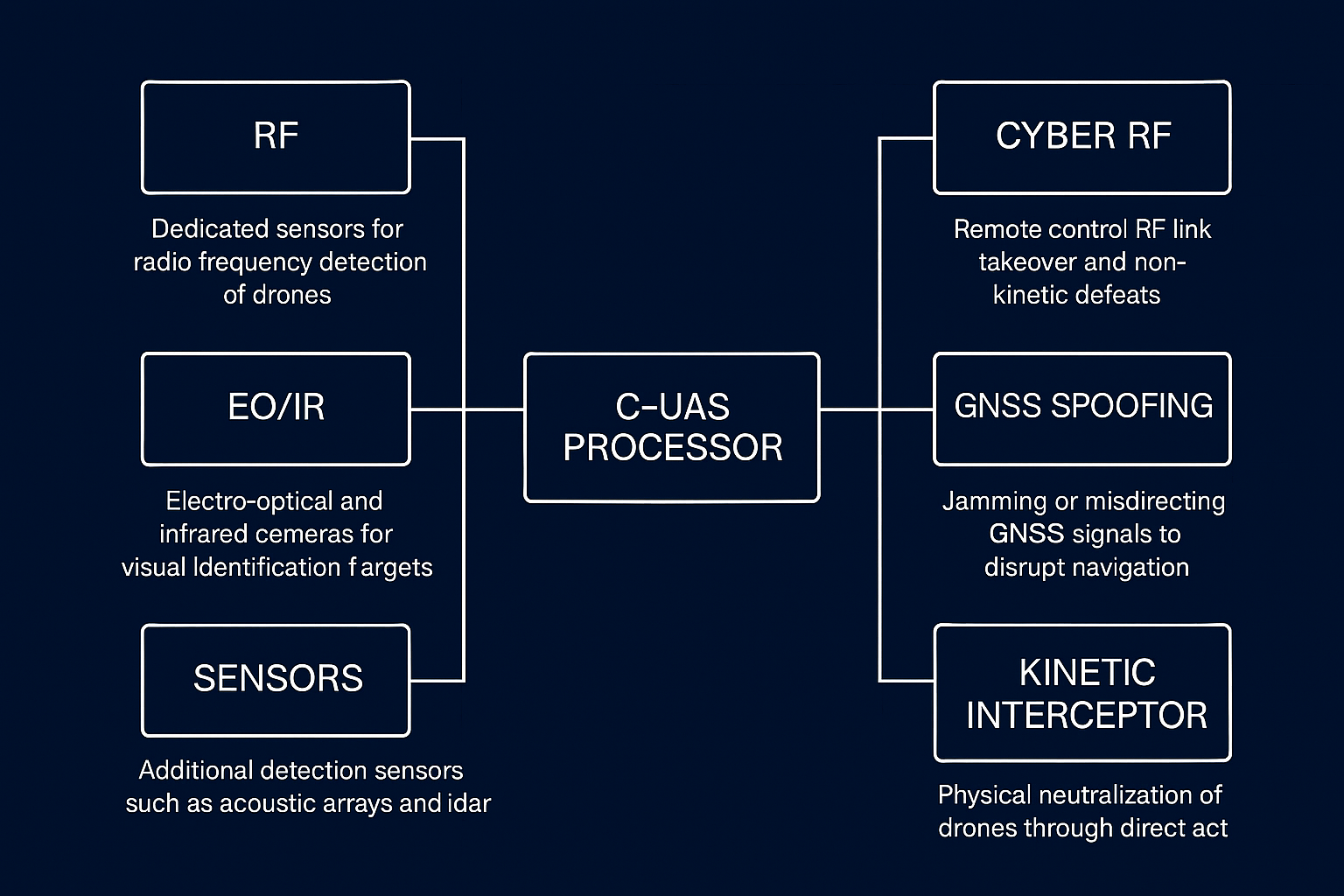
Cyber RF Takeover
Non-jamming, non-kinetic control that can land rogue drones at predefined safe zones, operating reliably in noisy/sensitive environments and distinguishing authorized from unauthorized drones.
- Combined RF detection, identification, and takeover in one SDR platform.
- Open API for integration with Command & Control and other sensors.